#Multi Domain Active Directory
Explore tagged Tumblr posts
Text
How to add a new Domain Controller to Existing Domain
A domain controller (DC) provides critical services like authentication and authorization for an Active Directory domain. More accurately, a DC runs on Windows Server operating system and that has Active Directory Domain Services (AD DS) installed on it. All these we will see very shortly. In this guide, we will learn how to how to add a new Domain Controller to Existing Domain. Please see how to…
#Add Domain Controller to Existing Domain#DC#Domain Controller#Domain Controller Setup#Microsoft Windows#Multi Domain Active Directory#Promote DC#Root Domain Controller#Secondary Domain Controller#Set Up a New Domain Controller for Replication#Windows#Windows Server#Windows Server 2012#Windows Server 2022#Windows Server 2025
0 notes
Text
Exploring the Depths: Active Directory Penetration Testing and the Enigma of Kerberos
Introduction
In the world of cybersecurity, staying one step ahead of potential threats is paramount. To safeguard an organization's sensitive information and network resources, it's crucial to regularly assess vulnerabilities and weaknesses. One potent approach is Active Directory (AD) penetration testing, which is an essential part of assessing and fortifying network security. This article delves into the intricacies of Active Directory penetration testing and the often elusive realm of Kerberos authentication.
Active Directory Penetration Testing: Unearthing Vulnerabilities
Active Directory, the cornerstone of identity management in Windows environments, serves as a centralized repository for user and system information, including authentication data. For cybercriminals, compromising AD can open the doors to a treasure trove of sensitive information. To counter this threat, organizations employ penetration testing to simulate real-world attacks and identify vulnerabilities.
Goals of Active Directory Penetration Testing
Identify Weak Passwords: One of the most common vulnerabilities is weak or easily guessable passwords. Penetration testers aim to uncover users with weak passwords and prompt them to strengthen their credentials.
Discover Misconfigured Permissions: Unauthorized access to resources can result from misconfigured permissions. Penetration testing assesses whether users have permissions that they shouldn't, potentially exposing sensitive data.
Locate Unpatched Systems: Outdated systems are susceptible to known vulnerabilities. Identifying and patching these systems is a critical goal of penetration testing.
Assess Kerberos Authentication: Active Directory relies heavily on Kerberos for secure authentication. Understanding Kerberos is essential for a thorough AD penetration test.
Kerberos: The Protector of Authentication
Kerberos, a network authentication protocol, plays a pivotal role in securing Active Directory environments. Named after the mythological three-headed dog guarding the gates of Hades, Kerberos acts as a guardian for network communication. Understanding how it works is vital for both defenders and attackers.
The Key Concepts of Kerberos
Authentication Tickets: In Kerberos, authentication occurs through tickets. A Ticket Granting Ticket (TGT) is obtained during initial authentication, and this TGT is used to request access to various resources without re-entering credentials.
Principle of Need to Know: Kerberos enforces the principle of "need to know." A user can access only the resources for which they have tickets, reducing the risk of unauthorized access.
Realms and Trust: In a multi-domain environment, Kerberos realms establish trust relationships between domains. Trust enables users from one domain to access resources in another.
Encryption: Kerberos relies on encryption to protect sensitive information, such as passwords and tickets. Encryption keys are generated dynamically during authentication.
Penetration Testing Kerberos: A Delicate Balancing Act
Penetration testing for Kerberos authentication involves a delicate balancing act between assessing security measures and not disrupting normal operations. Here are some critical aspects of Kerberos-focused penetration testing:
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak or vulnerable user accounts. Penetration testers attempt to retrieve Authentication Service (AS) tickets without the need for valid login credentials. This technique targets accounts with pre-authentication disabled, making them vulnerable to brute-force attacks.
2. Pass-the-Ticket Attacks
Pass-the-Ticket attacks involve stealing Ticket Granting Tickets (TGTs) from compromised systems. Attackers can then use these stolen TGTs to gain unauthorized access to other network resources. Penetration testing assesses the organization's ability to detect and defend against such attacks.
3. Golden Ticket Attacks
Golden Ticket attacks involve forging TGTs, effectively granting attackers unlimited access to the domain. Penetration testers may attempt to create Golden Tickets to evaluate the AD's resilience against this advanced attack.
4. Silver Ticket Attacks
Silver Tickets are used for unauthorized access to specific services or resources. A penetration test may focus on creating Silver Tickets to assess the AD's ability to detect and prevent such attacks.
11 notes
·
View notes
Text
Azure’s Evolution: What Every IT Pro Should Know About Microsoft’s Cloud
IT professionals need to keep ahead of the curve in the ever changing world of technology today. The cloud has become an integral part of modern IT infrastructure, and one of the leading players in this domain is Microsoft Azure. Azure’s evolution over the years has been nothing short of remarkable, making it essential for IT pros to understand its journey and keep pace with its innovations. In this blog, we’ll take you on a journey through Azure’s transformation, exploring its history, service portfolio, global reach, security measures, and much more. By the end of this article, you’ll have a comprehensive understanding of what every IT pro should know about Microsoft’s cloud platform.
Historical Overview
Azure’s Humble Beginnings
Microsoft Azure was officially launched in February 2010 as “Windows Azure.” It began as a platform-as-a-service (PaaS) offering primarily focused on providing Windows-based cloud services.
The Azure Branding Shift
In 2014, Microsoft rebranded Windows Azure to Microsoft Azure to reflect its broader support for various operating systems, programming languages, and frameworks. This rebranding marked a significant shift in Azure’s identity and capabilities.
Key Milestones
Over the years, Azure has achieved numerous milestones, including the introduction of Azure Virtual Machines, Azure App Service, and the Azure Marketplace. These milestones have expanded its capabilities and made it a go-to choice for businesses of all sizes.
Expanding Service Portfolio
Azure’s service portfolio has grown exponentially since its inception. Today, it offers a vast array of services catering to diverse needs:
Compute Services: Azure provides a range of options, from virtual machines (VMs) to serverless computing with Azure Functions.
Data Services: Azure offers data storage solutions like Azure SQL Database, Cosmos DB, and Azure Data Lake Storage.
AI and Machine Learning: With Azure Machine Learning and Cognitive Services, IT pros can harness the power of AI for their applications.
IoT Solutions: Azure IoT Hub and IoT Central simplify the development and management of IoT solutions.
Azure Regions and Global Reach
Azure boasts an extensive network of data centers spread across the globe. This global presence offers several advantages:
Scalability: IT pros can easily scale their applications by deploying resources in multiple regions.
Redundancy: Azure’s global datacenter presence ensures high availability and data redundancy.
Data Sovereignty: Choosing the right Azure region is crucial for data compliance and sovereignty.
Integration and Hybrid Solutions
Azure’s integration capabilities are a boon for businesses with hybrid cloud needs. Azure Arc, for instance, allows you to manage on-premises, multi-cloud, and edge environments through a unified interface. Azure’s compatibility with other cloud providers simplifies multi-cloud management.
Security and Compliance
Azure has made significant strides in security and compliance. It offers features like Azure Security Center, Azure Active Directory, and extensive compliance certifications. IT pros can leverage these tools to meet stringent security and regulatory requirements.
Azure Marketplace and Third-Party Offerings
Azure Marketplace is a treasure trove of third-party solutions that complement Azure services. IT pros can explore a wide range of offerings, from monitoring tools to cybersecurity solutions, to enhance their Azure deployments.
Azure DevOps and Automation
Automation is key to efficiently managing Azure resources. Azure DevOps services and tools facilitate continuous integration and continuous delivery (CI/CD), ensuring faster and more reliable application deployments.
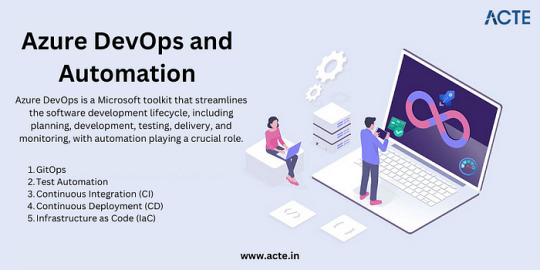
Monitoring and Management
Azure offers robust monitoring and management tools to help IT pros optimize resource usage, troubleshoot issues, and gain insights into their Azure deployments. Best practices for resource management can help reduce costs and improve performance.
Future Trends and Innovations
As the technology landscape continues to evolve, Azure remains at the forefront of innovation. Keep an eye on trends like edge computing and quantum computing, as Azure is likely to play a significant role in these domains.
Training and Certification
To excel in your IT career, consider pursuing Azure certifications. ACTE Institute offers a range of certifications, such as the Microsoft Azure course to validate your expertise in Azure technologies.

In conclusion, Azure’s evolution is a testament to Microsoft’s commitment to cloud innovation. As an IT professional, understanding Azure’s history, service offerings, global reach, security measures, and future trends is paramount. Azure’s versatility and comprehensive toolset make it a top choice for organizations worldwide. By staying informed and adapting to Azure’s evolving landscape, IT pros can remain at the forefront of cloud technology, delivering value to their organizations and clients in an ever-changing digital world. Embrace Azure’s evolution, and empower yourself for a successful future in the cloud.
#microsoft azure#tech#education#cloud services#azure devops#information technology#automation#innovation
2 notes
·
View notes
Text
SELinux in AOSP: A Guide to Securing Embedded Android Systems
Introduction
Security-Enhanced Linux (SELinux) is a core security mechanism in the Android Open Source Project (AOSP) that enforces robust access control. Unlike traditional Discretionary Access Control (DAC), which relies on user-based permissions, SELinux uses Mandatory Access Control (MAC) to restrict system interactions based on predefined policies. Android integrated SELinux starting from version 4.3. It runs in either permissive mode, which logs violations, or enforcing mode, which blocks unauthorized actions.

Understanding SELinux policies, labels, and domains is essential for embedded developers working on middleware, HAL, and system daemons in order to secure Android devices. Sensitive system components are protected, unauthorized access is limited, and privilege escalation is avoided with proper SELinux configuration. This blog discusses best practices for creating security policies, how SELinux functions within AOSP, and a real-world example of using SELinux on a binderized HAL. Developers can strengthen embedded systems against exploits and security breaches by becoming proficient with SELinux.
What is SELinux?
With mandatory access control (MAC) policies that limit programs' capabilities beyond conventional discretionary access controls (DAC), SELinux is a security architecture built into the Linux kernel. It guarantees that an application's activities stay contained within predetermined bounds even in the event that it is compromised.
Core Concepts of SELinux
Labels: Every process and object (like files, directories, and ports) in the system is assigned a security label. A key component of SELinux's decision-making process is these labels.
Type Enforcement (TE): The main SELinux mechanism is Type Enforcement (TE), in which policies specify how types (labels) linked to objects and processes can communicate. A process named httpd_t (Apache), for example, can be made to only access files with the label httpd_sys_content_t.
Roles and Users: To manage permissions more precisely, SELinux defines roles and users. Nonetheless, type enforcement continues to be the main focus in many implementations.
SELinux in AOSP
SELinux integration with Android
Google strengthened Android's security by integrating SELinux into the platform starting with version 4.3. SELinux functions in two ways in AOSP:
Permissive Mode: Violators are recorded but not stopped; SELinux rules are not enforced.
Enforcing Mode: SELinux rules are put into effect, and infractions are recorded and prevented. For strong security, Android devices try to run in enforcing mode.
Advantages of SELinux in Android
Privilege escalation is mitigated: SELinux restricts an application's behavior even if it acquires unauthorized privileges, avoiding more widespread system compromises.
Protection Against Malware: By limiting applications' access to private information or system components, SELinux policies can lessen the possible impact of malware.
Enhanced Multi-User Security: SELinux makes sure that user data is kept separate and safe from other users and applications by implementing stringent access controls.
Implementing SELinux in AOSP
Configuring the Linux kernel for SELinux: Make sure the kernel is compiled with SELinux support. This entails turning on particular security module configuration options.
Filesystem Labeling: Give filesystem objects the proper security labels. This can be accomplished by setting default labels in filesystem images or by using tools such as restorecon.
Compilation of Policies: Using tools like checkpolicy, create SELinux policies that are specific to the needs of your system.
Policy Loading: Use tools like load_policy or incorporate the compiled policies into the system's initialization procedure to load them into the kernel.
Writing SELinux Policies
IVI (In-Vehicle Infotainment), ADAS (Advanced Driver Assistance Systems), and telematics are among the vital services that Android Automotive OS (AAOS) manages in automotive embedded systems. SELinux policies are necessary to enforce stringent access controls across all system components, especially middleware services, Binderized HALs, and system daemons, in order to ensure security in such a system. In order to make sure that only authorized system components can access and alter vehicle data, we'll map SELinux policy writing to a real-world automotive example below using a binderized HAL.
Determine Types and Domains
Consider a Vehicle HAL (VHAL) in an automotive system, which gives users access to information about the vehicle, including its speed, fuel level, engine status, and door lock condition. The telematics module, navigation app, and IVI system are among the system elements with which the Vehicle HAL service communicates.
The hal_vehicle_t domain is where the Vehicle HAL daemon operates.
vehicle_data_t is the label for vehicle data files.
The ivi_system_t domain is where the IVI system operates.
The telematics_t domain is where the Telematics service functions.
By defining these domains, unauthorized applications are prevented from accessing vital vehicle parameters and controlled access between various system components is ensured.
Tools and Resources
SELinux Notebook: An open-source resource that provides comprehensive insights into SELinux concepts and implementations. GitHub - SELinuxProject/selinux-notebook
NSA's SELinux Implementation Report: An in-depth report detailing the implementation of SELinux as a Linux Security Module. Implementing SELinux as a Linux Security Module
Conclusion
With SELinux included in AOSP, developers can implement strict access controls, isolate processes, and keep sensitive information safe.
Whether you're building embedded Android systems, HAL layers, or automotive and IoT device middleware, SELinux offers a secure framework to ensure system integrity.
For any solution related to SELinux implementation, HAL hardening, or embedded Android security, connect with Silicon Signals at www.siliconsignals.io or email us at [email protected]. 👉 Do follow us on LinkedIn to stay updated on embedded tech insights and innovations.
#linux kernel#androidbsp#linuxdebugging#android#aosp#embeddedtechnology#embeddedsoftware#embeddedsystems#iot development services#selinux#linuxsecurity#aospsecurity
0 notes
Text
Mastering Windows Server 2019 Administration: A Guide for IT Professionals
Windows Server 2019, Microsoft’s robust and versatile server operating system, has become a cornerstone for organizations across various industries. Released as an evolution of the popular Windows Server 2016, it brings a suite of powerful features aimed at improving security, efficiency, and ease of management. Effective Windows Server 2019 administration involves understanding its capabilities, configuring its key settings, and leveraging its tools to meet organizational needs. This article explores the essentials of Windows Server 2019 administration, covering crucial components, best practices, and tips to help administrators make the most of this powerful system.
Key Features of Windows Server 2019
Windows Server 2019 builds upon its predecessors with several new features designed to optimize performance and security in modern data centers. Here are a few highlights that make it a standout choice for administrators:
Hybrid Cloud Support: With Azure integration, Windows Server 2019 offers seamless hybrid capabilities that allow administrators to connect on-premises servers with cloud services. This provides flexibility in managing workloads and extends the reach of IT infrastructure beyond physical boundaries.
Enhanced Security: Security remains a core focus of Windows Server 2019, with advanced features like Shielded Virtual Machines, Windows Defender ATP, and enhanced threat detection through Windows Defender Exploit Guard. These tools help protect against modern cybersecurity threats while reducing system vulnerabilities.
Improved Hyper-Converged Infrastructure (HCI): The HCI improvements in Windows Server 2019 enable administrators to manage storage, networking, and compute resources within a unified infrastructure, simplifying the management of virtualized environments.
Linux Integration: In recognition of the growing presence of Linux in enterprise environments, Windows Server 2019 offers built-in support for Linux containers, which allows administrators to run Linux-based applications and tools directly on Windows Server.
Storage Migration Services: Migrating servers to a new OS can be challenging, especially when dealing with critical data. The Storage Migration Service in Windows Server 2019 makes it easier to move servers from older systems by automatically transferring files, shares, and security configurations.

Core Responsibilities of Windows Server 2019 Administrators
Effective Windows Server 2019 administration requires a combination of technical skills and a solid understanding of organizational needs. Below are some of the primary responsibilities for administrators.
1. Setting Up and Configuring Servers
Setting up Windows Server 2019 begins with proper installation, followed by configuring network settings, Active Directory (AD), and role-based access. Administrators need to define specific roles for each server, such as DNS, DHCP, or file servers, to ensure streamlined operations. They also configure AD Domain Services to manage networked resources and enable centralized user management.
2. User and Access Management
One of the most critical aspects of server administration is managing user accounts and permissions. Windows Server 2019 simplifies this process through Active Directory, where administrators can create, modify, and control access for users, groups, and devices within the network. Properly setting up permissions and implementing Group Policies ensures that users have the right access levels while protecting sensitive data.
3. Implementing Security Protocols
Windows Server 2019 includes multiple layers of security to safeguard data and network resources. Security features such as Windows Defender, Credential Guard, and Exploit Guard help protect against threats. Configuring firewall settings, setting up intrusion detection, and implementing multi-factor authentication are all part of a comprehensive security protocol for ensuring data integrity and preventing unauthorized access.
4. Monitoring and Maintaining Performance
Performance monitoring is an ongoing task for Windows Server administrators. Using built-in tools like Windows Performance Monitor and Task Manager, administrators can track CPU usage, memory, disk activity, and network performance. Windows Admin Center provides a centralized dashboard for monitoring server health and performance, allowing administrators to identify issues and bottlenecks before they impact users.
5. Managing Backup and Recovery
Data backup and recovery plans are crucial for any organization, especially when downtime can lead to significant financial losses. Windows Server 2019 provides administrators with robust tools like Windows Server Backup and Volume Shadow Copy Service to schedule regular backups. In case of data loss or corruption, these tools enable quick recovery of data, minimizing downtime and ensuring business continuity.
6. Implementing Virtualization and Containerization
With Hyper-V, Windows Server 2019 supports extensive virtualization capabilities, allowing administrators to run multiple virtual machines on a single physical server. This enables efficient use of hardware resources and reduces operational costs. Additionally, container support allows administrators to deploy applications in isolated environments, making it easier to manage dependencies and streamline deployment.
Best Practices for Windows Server 2019 Administration
To ensure smooth and efficient server management, administrators should follow these best practices:
Regular Patching and Updating: Regular updates help keep the system secure and enhance performance. Using Windows Update and Windows Server Update Services (WSUS) ensures that servers are protected with the latest security patches.
Monitor Log Files: Log files can provide valuable insights into system health, user activities, and security events. Regularly monitoring logs can help detect unauthorized access attempts and resolve issues before they escalate.
Automate Routine Tasks: Automation tools like PowerShell scripts allow administrators to streamline repetitive tasks, such as user account management and data backups, saving time and reducing human error.
Create a Disaster Recovery Plan: Having a well-documented disaster recovery plan is crucial. This should include steps for data recovery, server restoration, and emergency contact information.
Conclusion
Windows Server 2019 is a powerful platform that offers extensive capabilities for managing and securing enterprise IT environments. Effective administration requires a deep understanding of its features, from hybrid cloud support and virtualization to advanced security and user management. By mastering these core components, administrators can ensure their organization’s infrastructure is reliable, secure, and scalable.
Adopting best practices, such as regular patching, automation, and disaster recovery planning, will further enhance an administrator’s ability to manage the server environment effectively. As businesses continue to rely on digital resources, Windows Server 2019 administrators play a crucial role in ensuring that the backbone of these systems is well-managed, resilient, and prepared for the future.
0 notes
Text
SaaS module for Perfex CRM Nulled Script 1.0.9

SaaS Module for Perfex CRM Nulled Script – Unlock Multitenancy for Ultimate Business Growth If you're looking to revolutionize your CRM platform, the SaaS module for Perfex CRM nulled script is your ultimate tool. This powerful extension transforms your Perfex CRM into a full-fledged SaaS-ready platform, supporting multitenancy and empowering you to launch your very own subscription-based CRM service. Whether you're a startup founder, developer, or digital entrepreneur, this module offers everything you need to scale and monetize your CRM offerings effortlessly. What is the SaaS Module for Perfex CRM Nulled Script? The SaaS module for Perfex CRM is a dynamic add-on designed to bring multitenancy functionality to your Perfex CRM. It enables you to host multiple client accounts under one central system, allowing each customer to manage their own CRM setup independently. This script is perfect for agencies and resellers looking to offer white-labeled CRM services without investing in separate installations for each client. Technical Specifications Platform Compatibility: Perfex CRM v2.9.0 and above License: GPL (Nulled) Multitenancy Support: Yes Custom Domain Support: Included Admin Dashboard: Multi-admin and sub-admin access Billing Integration: Stripe & PayPal Supported Automation: Auto instance creation for new users Key Features and Benefits 1. Full SaaS Conversion Transform your single-instance CRM into a revenue-generating SaaS model. The SaaS module for Perfex CRM nulled script automates client onboarding, billing, and CRM environment creation. 2. Streamlined Client Management Manage unlimited tenants from a single dashboard. Each tenant gets a fully isolated CRM environment, ensuring data privacy and security. 3. Subscription Billing Support Integrate Stripe or PayPal for recurring billing. Create multiple pricing tiers, offer trials, and scale your business effortlessly with built-in financial tools. 4. White-Labeling and Custom Branding Your clients won’t even know they’re using Perfex. The module allows full white-label support, including logos, custom domains, and personalized email configurations. 5. Easy Setup and Maintenance No coding required. Deploy new instances automatically with user registration, and perform updates across all accounts in one click. Real-World Use Cases Agencies: Provide a CRM solution for clients with your branding and pricing. Developers: Launch your SaaS business without building a CRM from scratch. Freelancers: Offer CRM-as-a-service with automated client onboarding and management. Installation Guide Installing the SaaS module for Perfex CRM nulled script is straightforward. Simply follow these steps: Download the nulled module package from our website. Upload the module to your Perfex CRM modules directory. Log into your admin dashboard and activate the module under "Modules Management." Configure your billing gateway, custom domains, and other settings. Start onboarding clients and monetizing your CRM! Frequently Asked Questions (FAQs) Q1: Is the SaaS module compatible with all Perfex CRM versions? A1: The module supports Perfex CRM version 2.9.0 and above. For best results, ensure your CRM is up to date. Q2: Can I use the nulled version for commercial purposes? A2: Yes, you can deploy the SaaS module for Perfex CRM nulled script commercially and offer it as a white-labeled service to clients. Q3: Are there any limitations in the nulled version? A3: No core features are limited. The nulled version is fully functional and ready for production environments. Q4: How do I handle updates and bug fixes? A4: Updates are frequently available through our platform. You can manually replace module files during updates. Download Now and Launch Your Own CRM SaaS Why build a SaaS CRM from scratch when you can have it all with the SaaS module for Perfex CRM nulled script? It’s fast, scalable, customizable, and ready for commercial deployment. Start your SaaS journey today by downloading this powerful tool from our collection.
Looking for more advanced tools? Check out our premium WordPress solutions like UpdraftPlus Premium nulled for effortless backup and restore capabilities. You can also find it externally at UpdraftPlus Premium nulled. Take the first step toward launching your own cloud CRM platform. Download the SaaS module for Perfex CRM now and start scaling your business like never before.
0 notes
Text
Boost Your Career with Microsoft Azure Security Engineer Associate Certification in Singapore
In an era where cybersecurity threats are constantly evolving, businesses are seeking skilled professionals to safeguard their cloud environments. The Microsoft Azure Security Engineer Associate certification in Singapore is one of the most sought-after credentials for IT professionals specializing in cloud security, compliance, and identity management. If you’re in Singapore and looking to advance your IT security career, obtaining this certification can open doors to numerous opportunities in the cybersecurity domain.
What is the Microsoft Azure Security Engineer Associate Certification?
The Microsoft Azure Security Engineer Associate certification is designed for IT professionals who secure Azure-based solutions and manage cloud security protocols effectively. It validates expertise in implementing security controls, identity management, threat protection, and data security within an Azure environment.
To achieve this certification, candidates must pass the AZ-500: Microsoft Azure Security Technologies exam, which covers key areas such as:
Managing identity and access using Azure Active Directory (Azure AD)
Implementing platform protection using Azure security tools
Managing security operations and incident response
Securing data and applications in cloud environments
Why Take the Microsoft Azure Security Engineer Associate Course in Singapore?
Singapore is a leading technology hub, with businesses and government organizations relying on Azure cloud solutions for digital transformation. Taking a Microsoft Azure Security Engineer Associate course in Singapore will provide you with structured training and hands-on experience to excel in cloud security roles. Here’s why you should enroll:
1. Learn from Certified Experts
Singapore-based training programs offer guidance from Microsoft-certified instructors with real-world expertise in Azure security, ensuring quality learning.
2. Hands-On Experience with Azure Security Tools
The course provides hands-on labs covering Microsoft Defender for Cloud, Azure Sentinel (Microsoft SIEM), and Azure Security Center, helping you gain practical skills.
3. High Demand for Cloud Security Professionals
With organizations migrating to the cloud, Azure Security Engineers are in high demand to protect cloud workloads and secure enterprise data.
4. Increase Your Earning Potential
Azure security certifications are highly valued, making you a competitive candidate for roles such as Cloud Security Engineer, Cybersecurity Analyst, and Security Architect.
5. Certification Exam Readiness
The course is designed to prepare you for the AZ-500 exam, ensuring you have the confidence to pass and earn your Microsoft Azure Security Engineer Associate credential.
Key Learning Areas in the Course
The Microsoft Azure Security Engineer Associate course in Singapore is structured to cover essential security principles, including:
Identity and Access Management – Learn how to implement and manage Azure AD, Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC) for identity security.
Platform Protection – Understand how to secure Azure resources using network security groups (NSGs), firewalls, and Just-In-Time (JIT) VM access.
Security Operations and Threat Protection – Gain expertise in Azure Sentinel, Microsoft Defender for Endpoint, and threat intelligence tools to detect and mitigate security threats.
Data and Application Security – Implement encryption, data loss prevention (DLP), and security policies to protect sensitive business data.
Monitoring and Incident Response – Learn how to configure security alerts, investigate threats, and respond to incidents using Azure Monitor and Log Analytics.
Who Should Enroll in This Course?
This course is ideal for:
IT professionals responsible for securing Azure cloud environments
Security analysts and engineers looking to specialize in cloud security
Network administrators seeking knowledge of Azure security operations
Individuals preparing for the AZ-500 certification exam
Why Choose a Microsoft Azure Security Course in Singapore?
Singapore is home to top IT training institutions offering flexible learning options, including in-person, virtual, and self-paced courses. Whether you are an IT professional working full-time or a student aspiring to enter the cybersecurity field, there is a course format that suits your needs.
Final Thoughts
Earning the Microsoft Azure Security Engineer Associate certification is a valuable investment in your cybersecurity career. With organizations prioritizing cloud security, this credential will give you a competitive edge and validate your expertise in securing Azure environments. By enrolling in a Microsoft Azure Security Engineer Associate course in Singapore, you will gain the necessary skills and practical knowledge to succeed in the cybersecurity industry.
0 notes
Text
Top-Quality Local SEO Services in India for Better Business Growth
In today's digital world, businesses need strong online visibility to attract local customers. Whether you own a small shop, a service-based company, or a multi-location business, best local SEO services can help you rank higher in search engine results. When customers search for products or services near them, a well-optimized local SEO strategy ensures your business appears at the top.

Why Local SEO is Important for Your Business
Local SEO focuses on improving your online presence for local searches. If your business operates in a specific city or region, you need local SEO service in India to boost traffic and sales. Here’s why local SEO is essential:
Increases Local Visibility: Most people use Google to find businesses near them. Local SEO ensures your business appears in Google Maps and local search results.
Attracts More Customers: Optimizing your business listing with accurate details like phone number, address, and reviews increases trust and encourages customers to visit your store.
Improves Website Traffic: When your business ranks higher for location-based keywords, more users visit your website, leading to increased conversions.
Builds Trust with Reviews: A strong local SEO strategy includes managing customer reviews, which play a major role in influencing buying decisions.
Key Strategies for Effective Local SEO
1. Google My Business Optimization
Google My Business (GMB) is one of the most important tools for local SEO. It allows you to manage your business listing, add images, respond to customer reviews, and provide accurate information. Ensure your business name, address, and phone number (NAP) are consistent across all online platforms.
2. Local Keyword Research
Choosing the right keywords is crucial for local SEO success. You should include location-based keywords relevant to your business. For example, if you provide local SEO services in Delhi, your keywords should include local SEO services in Delhi to attract potential clients in that area.
3. On-Page SEO Optimization
Your website content should be optimized with relevant local keywords. Key elements include:
Title tags and meta descriptions with location-based keywords.
High-quality, locally relevant content.
Proper URL structures that include city names.
Mobile-friendly and fast-loading pages.
4. Citation Building and NAP Consistency
Listing your business on online directories such as Justdial, Sulekha, and IndiaMART helps improve credibility. Make sure your NAP details remain the same across all platforms to avoid confusion among customers and search engines.
5. Customer Reviews and Ratings
Positive customer reviews improve your local rankings and build trust. Encourage happy customers to leave reviews on Google, Facebook, and other platforms. Respond to all reviews professionally, addressing both positive and negative feedback.
6. Local Link Building
Building local backlinks from trusted websites increases your domain authority. Partner with local businesses, get featured in online publications, and engage with community websites to gain quality links.
7. Social Media Engagement
Active social media profiles enhance your local presence. Posting engaging content, promoting offers, and interacting with local customers help drive traffic and build a loyal customer base.

Choosing the Right Local SEO Service Provider
Finding the right agency for local SEO is crucial to achieving success. If you are looking for expert services, Tech SEO Boost is a trusted company providing top-notch local SEO solutions. They specialize in:
Google My Business optimization
Local keyword research
On-page and off-page SEO
Review and reputation management
Local citation building
Website SEO audits
With years of experience and a proven track record, Tech SEO Boost ensures businesses improve their search rankings and gain more local customers.
Conclusion
Local SEO is a powerful tool to attract nearby customers and grow your business. With the best local SEO services, you can enhance your online visibility, drive more traffic, and boost sales. If you need a reliable local SEO service in India, partnering with professionals like Tech SEO Boost can help you achieve great results. Whether you are a startup or an established business, investing in local SEO services in Delhi is the key to staying ahead of the competition. Start optimizing today and watch your business thrive!
1 note
·
View note
Text
Mastering Windows Server 2019 Administration: A Guide for IT Professionals
Windows Server 2019, Microsoft’s robust and versatile server operating system, has become a cornerstone for organizations across various industries. Released as an evolution of the popular Windows Server 2016, it brings a suite of powerful features aimed at improving security, efficiency, and ease of management. Effective Windows Server 2019 administration involves understanding its capabilities, configuring its key settings, and leveraging its tools to meet organizational needs. This article explores the essentials of Windows Server 2019 administration, covering crucial components, best practices, and tips to help administrators make the most of this powerful system.
Key Features of Windows Server 2019
Windows Server 2019 builds upon its predecessors with several new features designed to optimize performance and security in modern data centers. Here are a few highlights that make it a standout choice for administrators:
Hybrid Cloud Support: With Azure integration, Windows Server 2019 offers seamless hybrid capabilities that allow administrators to connect on-premises servers with cloud services. This provides flexibility in managing workloads and extends the reach of IT infrastructure beyond physical boundaries.
Enhanced Security: Security remains a core focus of Windows Server 2019, with advanced features like Shielded Virtual Machines, Windows Defender ATP, and enhanced threat detection through Windows Defender Exploit Guard. These tools help protect against modern cybersecurity threats while reducing system vulnerabilities.
Improved Hyper-Converged Infrastructure (HCI): The HCI improvements in Windows Server 2019 enable administrators to manage storage, networking, and compute resources within a unified infrastructure, simplifying the management of virtualized environments.
Linux Integration: In recognition of the growing presence of Linux in enterprise environments, Windows Server 2019 offers built-in support for Linux containers, which allows administrators to run Linux-based applications and tools directly on Windows Server.
Storage Migration Services: Migrating servers to a new OS can be challenging, especially when dealing with critical data. The Storage Migration Service in Windows Server 2019 makes it easier to move servers from older systems by automatically transferring files, shares, and security configurations.

Core Responsibilities of Windows Server 2019 Administrators
Effective Windows Server 2019 administration requires a combination of technical skills and a solid understanding of organizational needs. Below are some of the primary responsibilities for administrators.
1. Setting Up and Configuring Servers
Setting up Windows Server 2019 begins with proper installation, followed by configuring network settings, Active Directory (AD), and role-based access. Administrators need to define specific roles for each server, such as DNS, DHCP, or file servers, to ensure streamlined operations. They also configure AD Domain Services to manage networked resources and enable centralized user management.
2. User and Access Management
One of the most critical aspects of server administration is managing user accounts and permissions. Windows Server 2019 simplifies this process through Active Directory, where administrators can create, modify, and control access for users, groups, and devices within the network. Properly setting up permissions and implementing Group Policies ensures that users have the right access levels while protecting sensitive data.
3. Implementing Security Protocols
Windows Server 2019 includes multiple layers of security to safeguard data and network resources. Security features such as Windows Defender, Credential Guard, and Exploit Guard help protect against threats. Configuring firewall settings, setting up intrusion detection, and implementing multi-factor authentication are all part of a comprehensive security protocol for ensuring data integrity and preventing unauthorized access.
4. Monitoring and Maintaining Performance
Performance monitoring is an ongoing task for Windows Server administrators. Using built-in tools like Windows Performance Monitor and Task Manager, administrators can track CPU usage, memory, disk activity, and network performance. Windows Admin Center provides a centralized dashboard for monitoring server health and performance, allowing administrators to identify issues and bottlenecks before they impact users.
5. Managing Backup and Recovery
Data backup and recovery plans are crucial for any organization, especially when downtime can lead to significant financial losses. Windows Server 2019 provides administrators with robust tools like Windows Server Backup and Volume Shadow Copy Service to schedule regular backups. In case of data loss or corruption, these tools enable quick recovery of data, minimizing downtime and ensuring business continuity.
6. Implementing Virtualization and Containerization
With Hyper-V, Windows Server 2019 supports extensive virtualization capabilities, allowing administrators to run multiple virtual machines on a single physical server. This enables efficient use of hardware resources and reduces operational costs. Additionally, container support allows administrators to deploy applications in isolated environments, making it easier to manage dependencies and streamline deployment.
Best Practices for Windows Server 2019 Administration
To ensure smooth and efficient server management, administrators should follow these best practices:
Regular Patching and Updating: Regular updates help keep the system secure and enhance performance. Using Windows Update and Windows Server Update Services (WSUS) ensures that servers are protected with the latest security patches.
Monitor Log Files: Log files can provide valuable insights into system health, user activities, and security events. Regularly monitoring logs can help detect unauthorized access attempts and resolve issues before they escalate.
Automate Routine Tasks: Automation tools like PowerShell scripts allow administrators to streamline repetitive tasks, such as user account management and data backups, saving time and reducing human error.
Create a Disaster Recovery Plan: Having a well-documented disaster recovery plan is crucial. This should include steps for data recovery, server restoration, and emergency contact information.
Conclusion
Windows Server 2019 is a powerful platform that offers extensive capabilities for managing and securing enterprise IT environments. Effective administration requires a deep understanding of its features, from hybrid cloud support and virtualization to advanced security and user management. By mastering these core components, administrators can ensure their organization’s infrastructure is reliable, secure, and scalable.
Adopting best practices, such as regular patching, automation, and disaster recovery planning, will further enhance an administrator’s ability to manage the server environment effectively. As businesses continue to rely on digital resources, Windows Server 2019 administrators play a crucial role in ensuring that the backbone of these systems is well-managed, resilient, and prepared for the future.
0 notes
Text
Local vs. Global SEO: Which Strategy Works Best for Your London Business?
In the ever-evolving world of digital marketing, Search Engine Optimization (SEO) is crucial for increasing your business’s visibility online. For businesses in London, deciding between a local SEO strategy and a global SEO strategy can significantly impact your online success. Each approach has its strengths, and the right choice for your London-based business depends on your target market, business model, and overall goals. This article will explore the differences between local and global SEO, and help you determine which strategy is best suited for your business.
What is Local SEO?
Local SEO focuses on optimizing your website and online presence to rank higher in local search results. It’s designed to attract customers in your immediate geographic area, making it especially useful for businesses that depend on local clientele or have a physical location. For instance, if you run a restaurant, a retail store, or a service-based business like plumbing or law in London, local SEO agency London is critical for reaching customers who are physically near your business.
Key components of local SEO include:
Google My Business Optimization: Setting up and optimizing your Google My Business profile, which helps your business appear in Google’s local search results, including Google Maps.
Local Keywords: Using keywords that reflect local intent, such as “best coffee shop in London” or “affordable plumber near me.”
Citations and Local Listings: Getting your business listed on local directories and industry-specific websites, which helps build your local authority.
Customer Reviews: Encouraging customer reviews on platforms like Google and Yelp, which not only boosts your credibility but also helps your local search rankings.
What is Global SEO?
Global SEO, on the other hand, focuses on optimizing your website to rank for a broader audience, typically at the national or international level. If your London-based business sells products or services that can be delivered globally, a global SEO strategy is more appropriate. This strategy focuses on targeting a wider range of keywords without geographic limitations, aiming for a higher search engine ranking across various regions and languages.
Key components of global SEO include:
Broad Keyword Targeting: Using keywords with global appeal, such as “buy shoes online” or “affordable software solutions.”
International SEO: Optimizing your website to cater to users from different countries, often involving multi-language and multi-country targeting.
Link Building: Acquiring backlinks from international websites to increase your domain authority and improve rankings on a global scale.
Content Marketing: Creating content that appeals to a global audience, ensuring it is culturally relevant and optimized for different languages if applicable.
Local SEO: The Right Fit for London-Based Businesses
For most London-based businesses, local SEO should be the primary focus. London is a competitive and dynamic market, and unless your business serves a global audience, there’s little benefit in targeting customers far beyond the city’s limits. By focusing on local SEO, you can increase your chances of being found by people actively searching for products or services in the area.
Here’s why local SEO works best for many London businesses:
Targeted Traffic: Local SEO targets users who are geographically close to your business, meaning the traffic you attract is more likely to convert into sales or leads. People searching for local businesses are often ready to make a purchase or book a service.
Competitive Advantage: Focusing on local SEO allows you to outrank competitors in your immediate area. If your business has a physical presence or is dependent on local foot traffic, appearing in local searches is crucial for success.
Increased Visibility in Google Maps: Google Maps has become a go-to tool for people looking for businesses nearby. Appearing in local search results and on Google Maps can significantly increase your visibility in the local market.
Global SEO: When to Consider It
While local SEO is typically more beneficial for businesses in London, there are cases where global SEO might be the right strategy. If your business operates in industries such as e-commerce, technology, or digital products that are not geographically restricted, global SEO can help you reach customers across the globe.
Here’s when global SEO might be more suitable:
E-commerce Businesses: If you run an online store that ships products worldwide, global SEO allows you to target customers in various countries. Optimizing your site for international search engines and targeting high-volume keywords can lead to more traffic and sales.
Global Service Providers: If your business provides services like digital marketing, consulting, or software development that can be accessed from anywhere in the world, global SEO ensures that you reach clients regardless of their location.
Brand Awareness: If you’re aiming to establish your business as an international brand, global SEO helps you reach new markets and build a global presence.
Key Differences Between Local and Global SEO
Target Audience: Local SEO focuses on a specific geographic area, while global SEO targets a wider audience across different regions or countries.
Keyword Strategy: Local SEO involves localized keywords (e.g., “London-based IT support”), while global SEO uses broader keywords (e.g., “IT support services”).
Ranking Factors: In local SEO, factors like proximity to the searcher, local reviews, and Google My Business optimization play a significant role. In global SEO, broader domain authority, backlinks from international sites, and the overall content quality are key ranking factors.
Competition: Local SEO often has less competition for niche keywords, as you’re targeting a more specific audience. In contrast, global SEO involves competing with businesses worldwide for high-traffic keywords.
Combining Local and Global SEO
For some businesses in London, a combination of local and global SEO strategies might be the best approach. For example, if you have a physical store in London but also sell products online to a global audience, you’ll need to target both local customers and international markets.
A combined strategy could include:
Local SEO for Storefront: Optimize for local search terms related to your physical location, helping you attract foot traffic and increase your visibility in your immediate area.
Global SEO for Online Sales: Focus on broader keywords for your e-commerce site and optimize your content for a global audience, using international SEO techniques to target various regions.
This hybrid approach ensures that your business reaches both local customers who visit your physical store and global customers who buy products or services online.
Conclusion
Deciding between local and global SEO ultimately depends on your business model and objectives. For most London-based businesses, local SEO is the most effective strategy to improve visibility and attract nearby customers. However, if your business serves an international market or sells globally, global SEO may be a better fit. In some cases, a combination of both strategies can deliver the best results. Working with an experienced SEO agency can help you determine the right approach and ensure that your online presence aligns with your business goals, leading to increased traffic, engagement, and sales.
0 notes
Text
Allow Multiple RDP Sessions on Windows Server: A Step-by-Step Guide
How to Enable Multiple Sessions [Windows Server and RDP] In this guide, you’ll learn how to enable multiple RDP sessions and resolve common issues that may arise. To connect to a machine using any remote desktop client, enable Remote Desktop and ensure users have authorization for RDP access. Keep in mind that desktop versions of Windows limit concurrent RDP sessions to one active user. run mulitple rdps This guide will also help you fix the “The Number of Connections to This Computer is Limited” error How to Enable Multiple Sessions [Windows Server and RDP].
By default, Windows Server disables multiple RDP sessions, meaning another administrator connecting will disconnect your session. Follow this tutorial to configure your server, allowing you to run multiple RDPs efficiently, whether on a single server or multiple servers.
Enable Multiple RDP Sessions Discover how to activate two RDP sessions and allow more than two. First, enable Remote Desktop on your PC.
rdp1 To enable multiple RDP connections, disable the restriction limiting the server to a single session per user, then adjust the maximum allowed connections.
Step 1. Activate Multiple RDP Connections Follow these steps to allow multiple RDP sessions on Windows Server:
Log in to your RDP server.
Press Windows Key + R to open the Run dialog.
Type gpedit.msc and press OK to open Local Group Policy Editor.
Navigate to: Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Connections
rdp2 Restrict Remote Desktop Services users to a single session: Set to Disabled and press OK. how to use multiple rdps at once using rdpwrap Limit number of connections: Set to Enabled, then increase the RD Maximum Connection allowed to 2.
rdp3 Note: If you set it more than 2, it won’t make any difference because you can make two concurrent sessions in this case! It’s done; now you should be able to have multiple RDP connections at the same time.
Step 2. Create New Remote Desktop Users To manage RDP sessions effectively, it’s best to create separate users. However, you can connect multiple times to RDP using the same user account!
Steps to Create Users:
Open Computer Management by typing compmgmt.msc in the Run dialog and pressing Enter.
Navigate to Computer Management (Local) -> Local Users and Groups -> Users. Right-click on Users and select New User. rdp4 Note: Add the newly created users to the Remote Desktop Users Group.
rdp5 Fill out the required fields and create as many users as needed (for now, just 2 users). Test your setup by connecting to RDP with two devices using different user accounts. woshub mulitple rdp Then, open Task Manager to view online users and their sessions.
rdp6 Using the above steps, you can Enable Multiple RDP Sessions successfully. Stay with us! There are so many to learn.
Allow More Than 2 Remote Sessions To enable more than two remote users, install Remote Desktop Services (RDS) enhanced multi user support for terminal servers windows 11. While an RDS license is required, installing RDS provides a 120-day free trial for this feature. Here, we’ll install RDS without using an ADDC (Active Directory Domain Controller).
Step 1. Install RDS
Open Server Manager.
In the Dashboard, select Add roles and features.
Choose Role-based or feature-based installation in the Installation Type step and click Next.
Select a server from the server pool in the Server Selection step and proceed.
Tick the Remote Desktop Service checkbox in the Server Roles step and click Next. rdp7 Proceed to the Features step with default options.
Tick Remote Desktop Connection Broker and Remote Desktop Session Host checkboxes, then click Next. Note 1: Accept any pre-required role services or features if prompted.
Note 2: To use RDS beyond the 120-day trial period, install the Remote Desktop Licensing role as well.
rdp8 In the final step, tick Restart the destination server automatically if required and click Install.
Note: Installation may take some time and might require several server reboots.
rdp9 Once done, increase the RD Maximum Connection allowed in the Limit number of connections file (e.g., 99) and set both files’ statuses as described earlier Buy RDP all locations.
How to Fix “The Number of Connections to
This Computer is Limited” When using Remote Desktop Protocol (RDP) to connect between Windows Server instances, users might encounter the “The Number of Connections to This Computer is Limited” error. This occurs when the session limit is reached, preventing further connections.
In this guide, you’ll learn how to fix this error using multiple solutions. When the maximum configured connections are reached, subsequent users will encounter this issue.
rdp 10 Server operating systems, like Windows Server or Linux, provide the platform for running applications. They ensure network connectivity and access to hardware resources. While RDP servers are a smart solution for remote work, they can face issues. Bugs causing server problems often occur in layers such as the Network, Hardware, or OS, but most are found in the application layer. Today, we’ll tackle one such issue and learn how to resolve it.
After purchasing a Windows RDP, configure it to support multiple concurrent RDP sessions, enabling separate sessions for different users. You can adjust the number of allowed simultaneous connections on your server.
If the “The number of connections to this computer is limited” error persists despite not exceeding the maximum allowed connections, this guide provides two solutions to resolve it.
Solutions to Fix “The Number of Connections to This Computer is Limited” Error If you frequently face the “The Number of Connections to this Computer is Limited” error, this guide provides steps to resolve it. After ensuring your RDP server is properly configured, test the following solutions. If your system is part of a domain, ask the domain controller to support this setup. Additionally, choosing a reliable RDP provider can prevent such errors.
For non-domain systems, disconnect the network cable, turn off WiFi, and restart the computer. After rebooting, reconnect the cable and activate WiFi. Linux RDP This often resolves the issue.
If the error persists, this tutorial offers two methods to fix it, letting you choose the best solution based on your system and expertise.
Solution 1: Check for the Number of Connected Users The error may occur because active RDP sessions remain disconnected. Some users close the RDP application without signing out, keeping their sessions open. To check:
Press Ctrl + Shift + Esc to open Task Manager. Go to the Users tab to view active users. rdp11 Right-click any column, select Session, and check the session types (RDP, console, terminal, etc.).
rdp12 Identify users connected via RDP and ensure their statuses are Disconnected. With this step, you’ve successfully applied the first technique to fix the error
rdp13 You have successfully finished the first technique to Fix the Number of Connections to this Computer is Limited Error.
Solution 2. Using GPO to Enable Multiple Remote Desktop Connections A Group Policy Object (GPO) is a collection of policy settings that could potentially cause issues. If the “The number of connections to this computer is limited” error persists, the second solution involves updating the Group Policy to allow multiple connections.
The RDP “The number of connections to this computer is limited” issue might have been resolved if you managed to update the Group Policy to permit multiple connections.
rdp14 Follow these steps:
Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections. rdp001 In the right pane, locate Limit Number of Connections and double-click it.
rdp16 Set it to Enabled, then enter your desired connection limit.
rdp17 Next, find and double-click Restrict Remote Desktop Services users to a single Remote Desktop Services session in the same pane.
rdp18 Set this option to Disabled to remove user restrictions.
rdp19 Finally, restart your computer for the changes to take effect. This will resolve the error by allowing multiple concurrent RDP connections.
Conclusion In this article, you learned how to enable multiple RDP sessions. To allow multiple RDP connections, you need to disable the single-user remote desktop mode and adjust the remote connection limit. This enables two RDP sessions simultaneously for free. However, if you need more, you must install the RDS role on the server. The RDS feature is free for 120 days, after which you must purchase an RDS license to continue using it.
This guide also covered how to fix “The Number of Connections to This Computer is Limited” error. Two solutions were explained to help you resolve the issue. If you have other methods or solutions, feel free to share them with us. By following the two solutions provided, you can easily fix the error. However, if any issues arise, don’t hesitate to contact us. Our technical support team will assist you in resolving any problems efficiently.
#how to use multiple rdps at once using rdpwrap#"woshub mulitple rdp#enhanced multi user support for terminal servers windows 11#Buy RDP all locations
0 notes
Text
Top 10 Skills Every Azure Administrator Should Master for the AZ-104 Exam

The AZ-104 exam, also known as the Microsoft Azure Administrator Associate certification, validates your skills in managing cloud services that span storage, security, networking, and compute capabilities within Microsoft Azure. It's a critical milestone for IT professionals looking to establish or advance their career in cloud administration. To ace this certification, mastering certain key skills is essential. Here’s a comprehensive look at the top 10 skills every Azure Administrator should develop:
1. Understanding Azure Core Services
Before diving into complex tasks, ensure a solid grasp of Azure's core services. These include Virtual Machines (VMs), Azure Storage, Virtual Networks, and Azure Active Directory. Understanding the basics of these services will provide a strong foundation for solving real-world problems and configuring advanced solutions. Focus on:
Deploying and managing VMs
Setting up Azure Resource Manager (ARM) templates
Configuring Azure Blob, File, and Disk Storage
2. Resource Management and Governance
Azure administrators must manage subscriptions, resource groups, and tags effectively to optimize costs and maintain an organized cloud environment. Key skills include:
Creating and managing Azure policies
Using Role-Based Access Control (RBAC) to assign permissions
Configuring and monitoring Azure Monitor and Log Analytics
Proficiency in resource management ensures your Azure infrastructure stays organized and adheres to governance standards.
3. Virtual Networking
Networking is the backbone of Azure infrastructure. Administrators need to design, implement, and manage virtual networks effectively. Key topics to focus on include:
Configuring Virtual Network (VNet) peering
Managing network security groups (NSGs) and application security groups (ASGs)
Implementing site-to-site, point-to-site, and virtual private network (VPN) gateways
Additionally, understanding Azure DNS and load balancing solutions like Azure Load Balancer and Azure Application Gateway is crucial.
4. Identity and Access Management
Azure administrators must ensure secure access to Azure resources. This involves a deep understanding of Azure Active Directory (Azure AD). Key focus areas include:
Managing Azure AD users and groups
Configuring Azure Multi-Factor Authentication (MFA)
Implementing conditional access policies
Integrating Azure AD with on-premises Active Directory
Strong identity and access management skills help ensure that only authorized users can access critical resources.
5. Azure Storage Management
Storage is a critical aspect of Azure. Understanding how to manage data efficiently is vital. You should be skilled in:
Implementing Azure Storage accounts
Configuring blob, table, queue, and file storage
Managing backups and configuring storage replication options
Implementing Azure File Sync for hybrid environments
These skills will help you manage large amounts of data while ensuring availability and redundancy.
6. Backup and Disaster Recovery
Business continuity is essential for any organization. Azure provides robust backup and disaster recovery solutions, and administrators should know how to configure them. Key areas to master include:
Setting up Azure Backup and Recovery Services
Implementing Azure Site Recovery (ASR) for disaster recovery
Configuring backup policies and restoring data from backups
These skills will enable you to ensure data integrity and minimize downtime during outages.
7. Monitoring and Troubleshooting
A proactive approach to monitoring and troubleshooting ensures that potential issues are identified and resolved promptly. Key skills in this domain include:
Setting up and interpreting Azure Monitor metrics and logs
Configuring alerts for resource utilization
Using Azure Advisor for best practice recommendations
Diagnosing connectivity and performance issues
Effective monitoring minimizes downtime and improves system performance.
8. Implementing and Managing Hybrid Environments
Many organizations operate in a hybrid cloud environment. Azure administrators should understand how to integrate and manage these setups. Focus on:
Configuring Azure Arc for hybrid and multi-cloud scenarios
Implementing VPN or ExpressRoute for connectivity
Using Azure Active Directory Connect to synchronize on-premises and cloud directories
Hybrid management skills are increasingly important in today’s interconnected IT landscapes.
9. Automation Using PowerShell and CLI
Automation is key to efficient Azure management. Familiarity with scripting and command-line tools can save time and reduce errors. Key areas include:
Writing PowerShell scripts for common administrative tasks
Using Azure Command-Line Interface (CLI) for resource management
Implementing Infrastructure as Code (IaC) with ARM templates and Bicep
Configuring automation workflows with Azure Automation and Logic Apps
Automation ensures consistency and scalability in Azure deployments.
10. Security Management
Security is paramount in any cloud environment. Azure administrators must ensure their systems are secure from external threats. Key skills include:
Implementing Azure Security Center and Azure Defender
Managing Azure Key Vault for secrets and certificates
Configuring Just-In-Time VM access
Understanding firewalls, encryption, and network segmentation
A strong focus on security management helps protect sensitive data and applications.
Tips for Success in the AZ-104 Exam
Study Microsoft Documentation: Microsoft’s official documentation provides comprehensive guidance for each topic in the AZ-104 syllabus.
Use Practice Tests: Leverage practice exams to identify weak areas and build confidence.
Hands-On Practice: Use the Azure portal and Azure free tier to experiment with real-world scenarios.
Join a Study Group: Collaborating with peers can help clarify complex concepts and provide additional resources.
Mastering these skills not only helps you succeed in the AZ-104 exam but also prepares you for a rewarding career as an Azure Administrator. With cloud adoption growing rapidly, your expertise in Azure administration will be in high demand across industries.
0 notes
Text
Microsoft Windows Server 2025 General Availability And Price

Introducing Windows Server 2025
With enhanced security, enhanced performance, and cloud agility, Windows Server 2025 is now widely available.
With its current general availability, Windows Server 2025 expands on its goal of providing a high-performance, secure Windows Server platform that can be customized to satisfy the various demands of its clients. Deploying apps in any environment on-premises, hybrid, or cloud will be possible with this release.
Windows Server 2025 features
Advanced multi-layered security
In a time when cybersecurity is critical, Windows Server 2025 stands out with some security capabilities that are intended to protect your infrastructure and data. The following are some essential skills:
The industry standard for identification and authentication, Active Directory (AD), continues to advance with new security features that help strengthen your environment against changing threats. These features include increased scalability, enhanced protocols, encryption, hardening, and additional cryptographic support.
Server message block (SMB) hardening: Windows Server 2025 has SMB over QUIC built in to allow safe online access to file sharing. Additionally, SMB security includes defenses against man-in-the-middle, relay, and spoofing attacks, as well as strengthened firewall defaults and the prevention of brute force assaults.
Unlike standard service accounts, Delegate Managed Service Accounts (dMSA) do not require manual password management because AD handles it automatically. Specific rights can be granted to access domain resources through dMSAs, which lowers security risks and improves service account activity visibility and logging.
Because of these cutting-edge security capabilities, Windows Server 2025 is a reliable and safe platform for your IT infrastructure that you should start assessing right away.
Windows Server 2025 new features
Cloud agility everywhere
A number of cutting-edge hybrid cloud features are introduced in Windows Server 2025 with the goal of improving operational flexibility and connectivity in a variety of settings. The following are important features:
Windows Server 2025 Hotpatching
Hotpatching made possible by Azure Arc: Users who run their entire business in the cloud benefit from built-in contemporary security features like backup and recovery and automatic software updates. It is now implementing some of those features for on-premises users of Windows Server 2025 through a new hotpatching subscription service that is made possible by Azure Arc. Customers will have fewer reboots and less operational disturbance with hotpatching. Hotpatching provides security updates for Azure Arc-enabled Windows Server 2025 Standard or Datacenter that are installed on on-premises, multicloud, virtual, or physical servers. Hotpatching, which is in preview right now, will cost a monthly fee. For Windows Server Datacenter Azure Edition virtual machines, the hotpatching capability is still free.
Easy onboarding for Azure Arc: Windows Server 2025 uses Azure Arc to deliver Azure’s potent capabilities straight to your datacenter. This integration improves operational flexibility and streamlines the onboarding process to Azure’s hybrid features, enabling you to better manage and secure your multicloud and hybrid environments.
Multisite aspects of software-defined networks (SDN): The software-defined network (SDN) multisite features provide unified network policy administration together with native L2 and L3 connection for smooth workload movement across many locations.
Unified network policy administration: This feature makes it simpler to maintain uniform security and performance requirements throughout your hybrid cloud system by enabling centralized management of network policies.
Because of these hybrid cloud features, Windows Server 2025 is a great option for businesses trying to maximize their IT infrastructure and take use of both on-premises and cloud settings.
AI, scale, and performance
The most demanding tasks, such as AI and machine learning, are intended to be handled by Windows Server 2025. These are a few essential skills:
AI, machine learning, and hyper-V: Windows Server 2025 provides a high-performance platform for both conventional applications and sophisticated AI workloads with live migration and high availability. It also has built-in support for GPU partitioning and can process massive data sets across distributed environments.
Performance of NVMe storage: On the same systems, Windows Server 2025 offers up to 60% higher storage IOPs than Windows Server 2022. (Based on Kioxia CM7 SSd and 4K randread with Diskpsd 2.2.)
Areas for Storage Direct and storage flexibility: For decades and even now, Windows Server has supported a variety of storage options, including local, NAS, and SAN. More storage innovation is provided by Windows Server 2025, which now comes with Storage Replica Compression, thinly provisioned Storage Spaces, and Native ReFS deduplication and compression in all editions.
Hyper-V performance and scalability: Azure’s performance and scalability enhancements are introduced in Windows Server 2025. Server 2025 for Windows Virtual machine maximums for Hyper-V:
Each virtual machine can have up to 240 Terabytes of RAM.
Maximum number of virtual processors per virtual machine: 2048 VPs* — (~8.5x before)
Hyper-V, GPU integration, Storage Spaces Direct (software defined storage), software-defined networking, and clustering all get significant improvements with Windows Server 2025. With these enhancements, Windows Server 2025 is a great choice for businesses seeking a virtualization solution and for businesses wishing to use AI and machine learning while still achieving high performance and scalability.
Access to System Center 2025 is now possible
System Center 2025 is delivered alongside Windows Server 2025, allowing you instant access to scalable Windows Server management. As a result, businesses can take full use of the latest capabilities in Windows Server. This version is expected to improve how businesses optimize their infrastructure and virtualized software-defined data centers, intending to improve agility, performance, and security. You may find out more by visiting the System Center 2025 site.
Windows Server 2025 price
Depending on your organization’s size, virtualization needs, and datacenter specifications, you can select between two main editions of Windows Server.
Standard edition
Suggested MSRP: $1,176
Ideal for physical or minimally virtualized environments
Core-based licensing model
Requires Windows Server CAL
Datacenter edition
Suggested MSRP: $6,771
Ideal for highly virtualized datacenters and cloud environments
Core-based licensing model
Requires Windows Server CAL
Windows Server 2025 Pay as you go
In order to accommodate capacity spikes or short-term seasonal demands, Windows Server Standard users who do not have unlimited virtualization can scale up with more virtual machines (VMs).
To transact, connect to Azure Arc.
Increase your agility
Only pay for what you require.
Microsoft Ignite 2024
Microsoft Ignite in Chicago on November 19–21. Many sessions will be accessible for online streaming for those of you who are unable to attend, including its Windows Server breakout titled Windows Server 2025: New Ways to Acquire Cloud Agility and security.
Microsoft offers its clients additional features on current versions of Windows Server, including 2016, 2019, 2022, and 2025. Customers with a valid subscription or Windows Server Software Assurance can utilize Azure administration tools such as Azure Update Manager, Azure Policy Guest Configuration, Disaster Recovery, Change Tracking and Inventory, and more. Many of these services are available at no additional cost. Stay tuned for additional demonstrations and details on how to utilize these new products at Microsoft Ignite.
Read more on Govindhtech.com
#MicrosoftWindows#WindowsServer#hybridcloud#machinelearning#AI#SystemCenter#virtualmachines#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
Boost Traffic & Authority: Essential Off-Page Submission Strategies for 2024
In Vadodara's thriving digital landscape, standing out from the crowd requires a multi-pronged SEO approach. While on-page optimization lays the groundwork, off-page submissions boosts your website's traffic and authority. Here at SEOWebPlanet, a leading provider of SEO services in Vadodara, we understand the ever-evolving SEO landscape. This blog dives deep into essential off-page submission strategies for 2024, empowering you to conquer search engine rankings and attract a wider audience.

Quality Backlinks Remain King (But with a Twist)
Backlinks, or incoming links from other websites is a major ranking factor for search engines. However, the focus shifts from quantity to quality. In 2024, prioritize acquiring backlinks from high-authority, relevant websites within your niche. This showcases search engines that your content is trustworthy and valuable.
Strategic Guest Blogging for Link Building and Brand Awareness
Guest blogging on reputable websites in Vadodara or catering to your target audience allows you to share your expertise,build relationships with other industry leaders, and secure valuable backlinks. Focus on creating high-quality, informative guest posts that resonate with the target audience of the host website. This not only strengthens your backlink profile but also expands your brand reach.
Broken Link Building: A Win-Win for Link Acquisition
Identify all the broken links on websites relevant to your industry. You can reach out to the webmaster and then suggest replacing those broken links with your content that offers similar value. This "broken link building" technique benefits both parties – you gain a valuable backlink, and the webmaster improves their website's user experience.
Industry Awards & Recognitions: A Credibility Booster
Being recognized for your digital marketing expertise can significantly enhance your website's authority. Consider applying for relevant industry awards in Vadodara or on a national level. Winning or being nominated can lead to positive press coverage, social media mentions, and valuable backlinks from award websites, all of which boost your online reputation.
Harness the Power of Online Directories and Business Listings
Ensure that your business is listed in prominent online directories and business listings that are industry-relevant. Focus on high-quality directories with a strong domain authority. Many local Vadodara directories exist, and claiming your profile allows you to control your business information, add links to your website, and improve local SEO.
Social Media Promotion: More Than Just Likes and Shares
Social media isn't just about building followers, it's about engaging your audience and driving traffic back to your website. Share informative and engaging content consistently, participate in relevant industry discussions, and run targeted social media campaigns to leverage the power of social media for SEO.
Building Relationships Through Forum Participation
Actively contribute to industry forums and online communities in Vadodara or catering to your target audience. Answer questions or share your knowledge, and establish yourself as a thought leader. Include a link back to your website in your forum signature, but prioritize providing valuable insights over blatant self-promotion.
Potential of Influencer Outreach
Partner with relevant influencers in Vadodara or your niche on social media or industry blogs. Collaborate on content creation, sponsor their activities, or offer them exclusive content to share with their audience. Influencer endorsements can significantly increase brand awareness, drive qualified traffic to your website, and potentially lead to backlinks.
Beyond Backlinks: Brand Mentions Matter Too
While backlinks are crucial, don't underestimate the power of unlinked brand mentions. Positive brand mentions online, whether in news articles, blog posts, or social media discussions, can significantly improve brand awareness and establish your authority in the eyes of search engines. Encourage brand mentions by creating high-quality content, engaging in online communities, and running effective public relations campaigns.
Conclusion: A Sustainable Off-Page SEO Strategy
Building a strong off-page SEO foundation requires a well-rounded strategy focused on quality over quantity. By implementing these essential off-page submission strategies in 2024, you can secure valuable backlinks that can help you enhance your brand reputation, and drive organic traffic to your website. Remember, SEO is a long-term game. Stay updated on the latest trends, consistently create high-quality content, and build genuine relationships within your industry for sustainable SEO success.
Looking for Help with Your Off-Page SEO Strategy?
At SEOWebPlanet, Vadodara's leading digital marketing agency, we offer comprehensive SEO services, including off-page optimization. Our expert team can help you develop strategies to build high-quality backlinks,improve your website's authority, and achieve your desired search engine ranking goals. Contact us today for a free consultation!
#seo#social media marketing#digital marketing services#local seo services#digital marketing company#targeted social media#SEO services in Vadodara#ppc#seo services#digital marketing#e-commerce#social media
0 notes
Text
Real-World Applications of RHCSA and RHCE Skills
The Red Hat Certified System Administrator (RHCSA) and Red Hat Certified Engineer (RHCE) certifications are highly regarded in the IT industry. These certifications validate an individual's skills in managing and automating Red Hat Enterprise Linux environments. However, the value of these certifications extends beyond just passing exams; the skills acquired are directly applicable to various real-world scenarios in the IT domain. Let's explore some of the practical applications of RHCSA and RHCE skills.
1. Server Management and Maintenance
RHCSA:
User and Group Management: Creating, modifying, and managing user accounts and groups. This is crucial for maintaining security and organization within a server environment.
File Permissions and ACLs: Setting appropriate permissions and access control lists to protect sensitive data and ensure users have the necessary access to perform their jobs.
Service Management: Starting, stopping, enabling, and disabling services using systemctl. This is essential for maintaining the uptime and performance of services.
RHCE:
Advanced System Monitoring: Using tools like top, htop, vmstat, and iotop to monitor system performance and diagnose issues.
Network Management: Configuring and troubleshooting network interfaces, firewalls, and SELinux settings to secure and optimize network communications.
2. Automating System Administration Tasks
RHCSA:
Shell Scripting: Writing basic scripts to automate repetitive tasks, such as backups, user creation, and log rotation.
Cron Jobs: Scheduling routine tasks to run automatically at specified times, ensuring consistent system maintenance without manual intervention.
RHCE:
Ansible Automation: Utilizing Ansible for configuration management and automation. Creating playbooks to automate complex multi-tier deployments and configurations.
Automating Deployments: Streamlining the process of deploying applications and services using automated scripts and configuration management tools.
3. System Security and Compliance
RHCSA:
Security Enhancements: Implementing basic security measures such as configuring firewalls with firewalld, and managing SELinux to enforce security policies.
Auditing and Logging: Setting up and maintaining system logs to monitor and audit system activities for compliance and troubleshooting purposes.
RHCE:
Advanced Security Configurations: Applying more sophisticated security measures such as configuring advanced SELinux policies, managing TLS/SSL certificates for secure communications, and implementing secure SSH practices.
System Auditing and Reporting: Using tools like auditd to create detailed security audits and reports, ensuring systems comply with security policies and standards.
4. Troubleshooting and Problem Solving
RHCSA:
Basic Troubleshooting: Using commands like journalctl, dmesg, and systemctl to diagnose and resolve common issues related to system performance, boot processes, and service failures.
Disk Management: Managing storage with LVM (Logical Volume Management) and understanding disk usage with tools like df and du.
RHCE:
Advanced Troubleshooting: Diagnosing complex issues involving network services, storage systems, and application performance. Using advanced tools and techniques to pinpoint and resolve problems.
System Recovery: Implementing disaster recovery plans, including restoring from backups, repairing boot issues, and recovering corrupted file systems.
5. Managing Enterprise Environments
RHCSA:
Package Management: Installing, updating, and managing software packages using yum or dnf, ensuring that systems have the necessary software and updates.
Network Configuration: Setting up and managing basic network configurations, including IP addresses, DNS settings, and hostname configurations.
RHCE:
Centralized Authentication: Setting up and managing centralized authentication services such as LDAP, Kerberos, and integrating with Active Directory.
Clustering and High Availability: Configuring and managing Red Hat High Availability Clustering to ensure critical services are always available.
6. DevOps and Continuous Integration/Continuous Deployment (CI/CD)
RHCSA:
Version Control Systems: Basic knowledge of version control systems like Git, which is fundamental for managing code and configuration files.
Containerization: Introduction to containerization concepts using tools like Docker.
RHCE:
CI/CD Pipelines: Setting up and managing CI/CD pipelines using tools like Jenkins, GitLab CI, or Red Hat OpenShift, enabling automated testing, integration, and deployment of applications.
Advanced Container Management: Managing and orchestrating containers using Kubernetes and Red Hat OpenShift, ensuring scalable and reliable deployment of containerized applications.
Conclusion
The skills acquired through RHCSA and RHCE certifications are not just theoretical but have direct, practical applications in the real world. Whether it's managing and securing servers, automating administrative tasks, or setting up robust enterprise environments, these certifications equip IT professionals with the knowledge and tools necessary to excel in their careers. By applying these skills, professionals can ensure efficient, secure, and high-performing IT operations, ultimately driving organizational success.
For more details click www.qcsdclabs.com
#redhatcourses#information technology#containerorchestration#kubernetes#docker#linux#container#qcsdclabs#rhcsa#rhce#devops#ansibleautomation
1 note
·
View note
Text
how to setup dns with azure hybrid ad vpn
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
how to setup dns with azure hybrid ad vpn
DNS-Einrichtung
Die DNS-Einrichtung, die für Domain Name System steht, ist ein wesentlicher Bestandteil des Internets und ermöglicht es, dass Menschen mit Websites interagieren können. Es ist sozusagen wie ein Adressbuch des Internets, das dafür sorgt, dass wenn jemand eine Website besuchen möchte, der richtige Weg gefunden wird.
Die Einrichtung des DNS umfasst verschiedene Schritte, beginnend mit der Registrierung einer Domain bei einem Domain-Registrar. Dabei wird die Domain mit den entsprechenden DNS-Servern verknüpft, die die IP-Adressen der Website speichern. Dies ermöglicht es, dass wenn jemand den Domainnamen in einen Webbrowser eingibt, die richtige Webseite aufgerufen wird.
Es ist wichtig, die DNS-Einstellungen richtig zu konfigurieren, um eine reibungslose Verbindung zu gewährleisten. Dazu gehören die Einstellung der Nameserver, die Weiterleitung, die Erstellung von DNS-Einträgen wie A-, CNAME-, MX- und TXT-Records sowie die Überwachung der DNS-Leistung.
Es gibt auch spezialisierte DNS-Anbieter, die erweiterte Funktionen wie schnellere DNS-Auflösungen, Sicherheitsfunktionen und Traffic-Management anbieten. Durch die Auswahl des richtigen DNS-Anbieters kann die Leistung und Sicherheit der Website optimiert werden.
Insgesamt ist die DNS-Einrichtung ein wichtiger Schritt bei der Erstellung einer Website und trägt dazu bei, dass Benutzer fehlerfrei auf die gewünschten Webinhalte zugreifen können. Es ist daher ratsam, sich mit den Grundlagen der DNS-Konfiguration vertraut zu machen oder einen Experten hinzuzuziehen, um sicherzustellen, dass alles reibungslos funktioniert.
Azure Hybrid AD
Azure Hybrid AD (Active Directory) ermöglicht Unternehmen, ihre lokale Active Directory-Umgebung nahtlos mit der Cloud zu verbinden. Dies bietet eine Vielzahl von Vorteilen, darunter eine verbesserte Sicherheit, vereinfachtes Identitätsmanagement und eine höhere Flexibilität für Benutzer. Durch die Integration von lokalen AD-Strukturen mit Azure AD können Unternehmen eine Hybrididentitätslösung implementieren, die das Beste aus beiden Welten kombiniert.
Mit Azure Hybrid AD können Benutzer auf Ressourcen sowohl in der Cloud als auch vor Ort mit denselben Anmeldeinformationen zugreifen. Dadurch wird die Benutzererfahrung verbessert und die Notwendigkeit für separate Anmeldeinformationen eliminiert. Zusätzlich ermöglicht Azure Hybrid AD eine verbesserte Sicherheit durch Funktionen wie Multi-Faktor-Authentifizierung und sicherem Kennwort-Hashing.
Darüber hinaus bietet Azure Hybrid AD Unternehmen die Möglichkeit, von der Skalierbarkeit und Flexibilität der Cloud zu profitieren, ohne ihre lokale AD-Infrastruktur aufgeben zu müssen. Dies ermöglicht es Unternehmen, schrittweise in die Cloud zu migrieren und ihre lokale AD-Strukturen zu modernisieren, ohne sofort alle ihre Serverressourcen aufgeben zu müssen.
Insgesamt bietet Azure Hybrid AD eine leistungsstarke Lösung für Unternehmen, die die Vorteile der Cloud nutzen möchten, ohne ihre vorhandenen lokalen AD-Strukturen zu opfern. Durch die nahtlose Integration von lokalen und Cloud-Identitätslösungen können Unternehmen ihre Sicherheit verbessern, die Benutzererfahrung optimieren und gleichzeitig ihre Flexibilität wahren.
VPN-Konfiguration
Eine VPN-Konfiguration, oder Virtual Private Network-Konfiguration, bezieht sich auf die Einstellungen, die erforderlich sind, um eine sichere Verbindung zu einem VPN-Server herzustellen. VPN wird häufig verwendet, um die Privatsphäre und Sicherheit bei der Internetnutzung zu erhöhen.
Um eine VPN-Konfiguration durchzuführen, müssen Benutzer normalerweise ihre VPN-Software öffnen und die erforderlichen Einstellungen vornehmen. Dies kann das Auswählen eines bestimmten VPN-Servers, das Festlegen von Verschlüsselungsoptionen und das Einrichten von Zugangsdaten umfassen. Einige VPN-Anbieter bieten auch vorkonfigurierte Optionen für eine einfache und schnelle Einrichtung.
Eine VPN-Konfiguration kann auf verschiedenen Geräten durchgeführt werden, einschließlich Computern, Smartphones, Tablets und Routern. Durch die Verwendung einer VPN-Verbindung können Benutzer ihre IP-Adresse verbergen, ihren Standort verschleiern und ihre Daten vor neugierigen Blicken schützen.
Es ist wichtig zu beachten, dass eine ordnungsgemäße VPN-Konfiguration eine vertrauenswürdige und zuverlässige VPN-Software erfordert. Benutzer sollten sicherstellen, dass sie einen seriösen VPN-Anbieter auswählen, um die bestmögliche Verschlüsselung und Sicherheit zu gewährleisten.
Zusammenfassend kann eine VPN-Konfiguration eine effektive Methode sein, um die Privatsphäre und Sicherheit im Internet zu verbessern. Mit den richtigen Einstellungen können Benutzer eine verschlüsselte Verbindung herstellen und ihre Online-Aktivitäten vor potenziellen Bedrohungen schützen.
Netzwerkverbindung
Eine Netzwerkverbindung ist eine entscheidende Komponente in der heutigen digitalen Welt. Sie ermöglicht es Geräten, miteinander zu kommunizieren und Ressourcen wie Dateien, Drucker und das Internet gemeinsam zu nutzen. Es gibt verschiedene Arten von Netzwerkverbindungen, darunter kabelgebundene Verbindungen wie Ethernet und drahtlose Verbindungen wie WLAN.
Kabelgebundene Netzwerkverbindungen werden häufig in Büroumgebungen und Rechenzentren eingesetzt, da sie eine zuverlässige und schnelle Verbindung bieten. Ethernet-Kabel werden verwendet, um Geräte wie Computer, Router und Switches miteinander zu verbinden und den Datenaustausch zu ermöglichen.
Drahtlose Netzwerkverbindungen sind in privaten Haushalten und öffentlichen Einrichtungen weit verbreitet. WLAN ermöglicht es Geräten, über Funkwellen miteinander zu kommunizieren, ohne dass physische Kabel benötigt werden. Dies bietet eine flexible Möglichkeit, Geräte zu verbinden und ermöglicht es Benutzern, sich frei zu bewegen, während sie weiterhin mit dem Netzwerk verbunden sind.
Eine zuverlässige Netzwerkverbindung ist entscheidend für eine reibungslose Kommunikation und Datenaustausch zwischen Geräten. Durch die Auswahl der geeigneten Art der Netzwerkverbindung und die ordnungsgemäße Konfiguration können Benutzer sicherstellen, dass ihre Geräte optimal miteinander verbunden sind, um effizient und effektiv zusammenarbeiten zu können.
Sicherheitsrichtlinien
Sicherheitsrichtlinien sind grundlegende Regeln und Maßnahmen, die dazu dienen, die Sicherheit von Personen, Informationen oder Einrichtungen zu gewährleisten. Sie sind in verschiedenen Bereichen von entscheidender Bedeutung, insbesondere im Bereich der Informationstechnologie, im Gesundheitswesen, im Bauwesen und vielen anderen Branchen.
Im Bereich der Informationstechnologie sind Sicherheitsrichtlinien Richtlinien und Verfahren, die von Unternehmen festgelegt werden, um sicherzustellen, dass sensible Daten und Informationen vor unbefugtem Zugriff, Manipulation oder Diebstahl geschützt sind. Dazu gehören Passwortrichtlinien, Datensicherungsvorschriften, Zugriffskontrollen und vieles mehr.
Im Gesundheitswesen dienen Sicherheitsrichtlinien dazu, die Vertraulichkeit und Integrität von Patientendaten zu gewährleisten. Dies umfasst Maßnahmen zur sicheren Aufbewahrung von Akten, zur sicheren Übertragung von Daten und zum Schutz vor Cyberangriffen.
Im Bauwesen legen Sicherheitsrichtlinien Verfahren fest, um Unfälle am Arbeitsplatz zu vermeiden und die Gesundheit und Sicherheit der Arbeiter zu gewährleisten. Dazu gehören Vorschriften zur Verwendung persönlicher Schutzausrüstung, zur Einhaltung von Sicherheitsabständen und zur Schulung der Mitarbeiter.
Insgesamt sind Sicherheitsrichtlinien unerlässlich, um Gefahren zu minimieren, Risiken zu kontrollieren und ein sicheres Arbeitsumfeld zu schaffen. Unternehmen und Organisationen sollten Sicherheitsrichtlinien immer ernst nehmen und regelmäßig überprüfen und aktualisieren, um mit den aktuellen Bedrohungen und Herausforderungen Schritt zu halten.
0 notes